- USDT(TRC-20)
- $0.0
When Apple dropped macOS Sequoia last month, it added new features like window snapping and the ability to control your iPhone from your Mac. In addition to surface-level changes, however, the new update also introduced a lengthy series of patches for security vulnerabilities. As it happens, one of these vulnerabilities was discovered by none other than Microsoft, and is quite concerning for Macs used within organizations.
Microsoft described its findings in a blog post on Oct. 17, just about one month after the Sept. 16 release of macOS Sequoia. The company calls the flaw "HM Surf," named after the teachable move in the Pokémon series, which they discovered allows bad actors to bypass Apple's Transparency, Consent, and Control platform for Safari. TCC typically ensures that apps without proper permission cannot access services like your location, camera, or microphone. It's essential for preserving your privacy from apps that would otherwise like to abuse it.
However, Apple gives some of its own apps entitlements that allow them to bypass these TCC roadblocks. It's Apple's app, after all, so the company knows it isn't malicious. In Safari's case, Microsoft found the app has access to your Mac's address book, camera, and microphone, among other services, without needing to go through TCC checks first.
All that said, you still encounter TCC checks while using Safari across websites: That's what happens when you load a page, and a pop-up asks if you'll allow the site access to something like your camera. Those TCC settings per website are saved to a directory on your Mac under ~/Library/Safari.
This is where the exploit comes in: Microsoft discovered you can change this directory to a different location, which removes the TCC protections. Then, you can modify sensitive files in the real home directory, then change the directory back, so Safari pulls from the modified files you put in place. Congratulations: You're now able to bypass TCC protections, and take a picture with the Mac's webcam, as well as access location information for the machine.
Microsoft says there are a number of actions bad actors could potentially take from this situation, including saving the webcam picture somewhere they can access it later; record video from your webcam; stream audio from your microphone to an outside source; and run Safari in a small window, so you don't notice its activity. Importantly, third-party browsers are not affected here, as they have to deal with Apple's TCC requirements, and do not have Safari's entitlements to bypass them.
While Microsoft did find suspicious activity in its investigation that might indicate this vulnerability has been exploited, it could not say for sure.
After reading Microsoft's report, ou might be worried about the prospect of bad actors snooping on your Mac through Safari. However, what isn't made explicit here is this vulnerability only affects MDM-managed Macs, i.e. Macs belonging to organizations controlled by a central IT service. That includes Macs issued to you from your job, or a computer belonging to your school.
Apple confirms as much in its security notes for macOS Sequoia, in a rather brief entry considering the privacy and security implications:
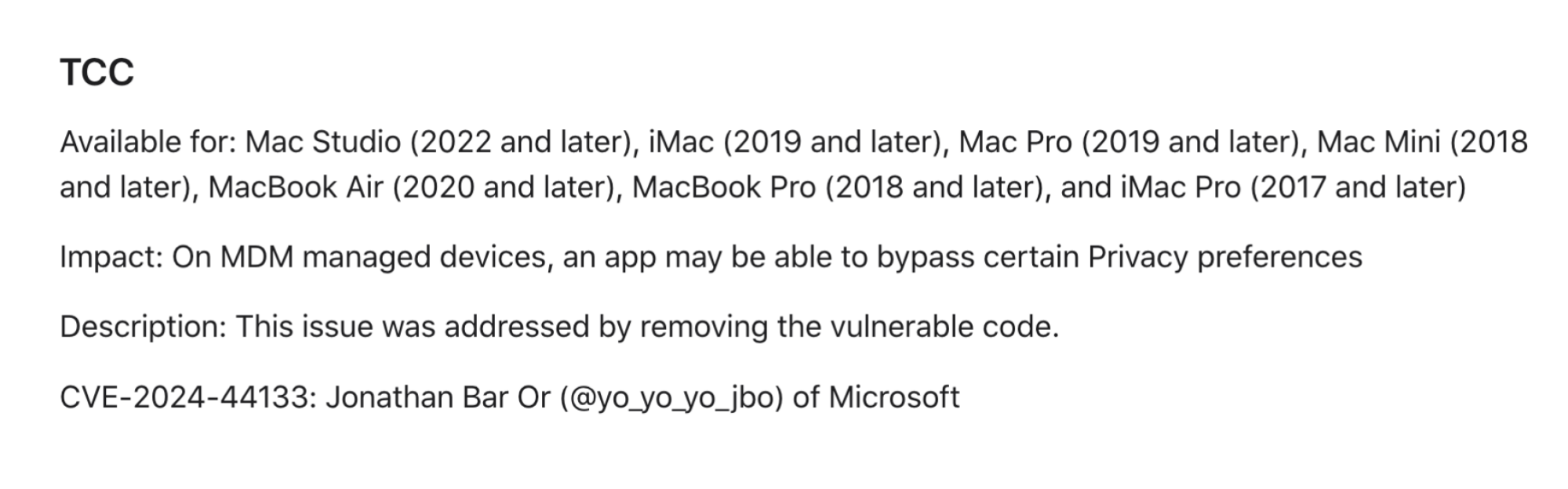
Credit: Apple
Of course, the flaw is still serious, but it is much more limited. You don't have to worry about Safari on your personal Mac allowing hackers to access your webcam, microphone, and location. But if you do have a Mac issued from work or school that is MDM-managed, that is a concern, and you should install the update as soon as possible.
This flaw affects the following Macs: Mac Studio (2022 and later), iMac (2019 and later), Mac Pro (2019 and later), Mac Mini (2018 and later), MacBook Air (2020 and later), MacBook Pro (2018 and later), and iMac Pro (2017 and later).
It's possible your organization has already issued the update for your Mac, if it's eligible. However, if your machine isn't running macOS Sequoia, check with your company or school's IT to see when an update will become available.
Full story here:
How Safari's TCC flaw works
Microsoft described its findings in a blog post on Oct. 17, just about one month after the Sept. 16 release of macOS Sequoia. The company calls the flaw "HM Surf," named after the teachable move in the Pokémon series, which they discovered allows bad actors to bypass Apple's Transparency, Consent, and Control platform for Safari. TCC typically ensures that apps without proper permission cannot access services like your location, camera, or microphone. It's essential for preserving your privacy from apps that would otherwise like to abuse it.
However, Apple gives some of its own apps entitlements that allow them to bypass these TCC roadblocks. It's Apple's app, after all, so the company knows it isn't malicious. In Safari's case, Microsoft found the app has access to your Mac's address book, camera, and microphone, among other services, without needing to go through TCC checks first.
All that said, you still encounter TCC checks while using Safari across websites: That's what happens when you load a page, and a pop-up asks if you'll allow the site access to something like your camera. Those TCC settings per website are saved to a directory on your Mac under ~/Library/Safari.
This is where the exploit comes in: Microsoft discovered you can change this directory to a different location, which removes the TCC protections. Then, you can modify sensitive files in the real home directory, then change the directory back, so Safari pulls from the modified files you put in place. Congratulations: You're now able to bypass TCC protections, and take a picture with the Mac's webcam, as well as access location information for the machine.
Microsoft says there are a number of actions bad actors could potentially take from this situation, including saving the webcam picture somewhere they can access it later; record video from your webcam; stream audio from your microphone to an outside source; and run Safari in a small window, so you don't notice its activity. Importantly, third-party browsers are not affected here, as they have to deal with Apple's TCC requirements, and do not have Safari's entitlements to bypass them.
While Microsoft did find suspicious activity in its investigation that might indicate this vulnerability has been exploited, it could not say for sure.
This vulnerability only affects MDM-managed Macs
After reading Microsoft's report, ou might be worried about the prospect of bad actors snooping on your Mac through Safari. However, what isn't made explicit here is this vulnerability only affects MDM-managed Macs, i.e. Macs belonging to organizations controlled by a central IT service. That includes Macs issued to you from your job, or a computer belonging to your school.
Apple confirms as much in its security notes for macOS Sequoia, in a rather brief entry considering the privacy and security implications:

Credit: Apple
Of course, the flaw is still serious, but it is much more limited. You don't have to worry about Safari on your personal Mac allowing hackers to access your webcam, microphone, and location. But if you do have a Mac issued from work or school that is MDM-managed, that is a concern, and you should install the update as soon as possible.
Patching the flaw on your MDM-managed Mac
This flaw affects the following Macs: Mac Studio (2022 and later), iMac (2019 and later), Mac Pro (2019 and later), Mac Mini (2018 and later), MacBook Air (2020 and later), MacBook Pro (2018 and later), and iMac Pro (2017 and later).
It's possible your organization has already issued the update for your Mac, if it's eligible. However, if your machine isn't running macOS Sequoia, check with your company or school's IT to see when an update will become available.
Full story here:


