This is a cross platform python framework which allows you to build custom payloads for Windows, Mac OSX and Linux as well. You are able to select whether the payload binds to a specific IP and port, listens for a connection on a port, option to send an email of system info when the system boots, and option to start keylogger on boot. Payloads created can only run on the OS that they were created on.
Features
Cross Platform Support
- Command and file auto-completion
- Antivirus detection
- Able to turn off/on display monitors
- Hide/unhide files and directories
- View/edit the hosts file
- View all the systems environment variables
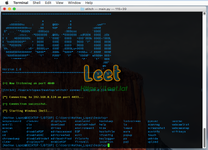
- Keylogger with options to view status, start, stop and dump the logs onto your host system
- View the location and other information of the target machine
- Execute custom python scripts which return whatever you print to screen
- Screenshots
- Virtual machine detection
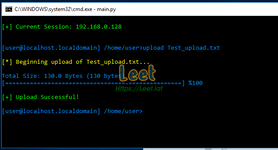
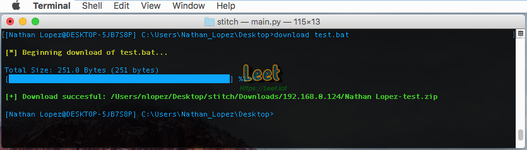
- Download/Upload files to and from the target system
- Attempt to dump the systems password hashes
- Payloads' properties are "disguised" as other known programs
Windows Specific
- Display a user/password dialog box to obtain user password
- Dump passwords saved via Chrome
- Clear the System, Security, and Application logs
- Enable/Disable services such as RDP,UAC, and Windows Defender
- Edit the accessed, created, and modified properties of files
- Create a custom popup box
- View connected webcam and take snapshots
- View past connected wifi connections along with their passwords
- View information about drives connected
- View summary of registry values such as DEP
Mac OSX Specific
- Display a user/password dialog box to obtain user password
- Change the login text at the user's login screen
- Webcam snapshots
Mac OSX/Linux Specific
- SSH from the target machine into another host
- Run sudo commands
- Attempt to bruteforce the user's password using the passwords list found in Tools/
- Webcam snapshots? (untested on Linux)
Implemented Transports
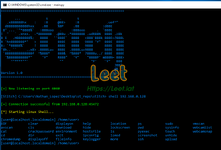
All communication between the host and target is AES encrypted. Every Stitch program generates an AES key which is then put into all payloads. To access a payload the AES keys must match. To connect from a different system running Stitch you must add the key by using the showkey command from the original system and the addkey command on the new system.
Implemented Payload Installers
The "stitchgen" command gives the user the option to create NSIS installers on Windows and Makeself installers on posix machines. For Windows, the installer packages the payload and an elevation exe ,which prevents the firewall prompt and adds persistence, and places the payload on the system. For Mac OSX and Linux, the installer places the payload and attempts to add persistence. To create NSIS installers you must download and install NSIS.
How To Run
python main.pyor
./main.py
Download
More Screenshots